After you installed LAM you can configure it to fit your needs. The complete configuration can be done inside the application. There is no need to edit configuration files.
Please point you browser to the location where you installed LAM. E.g. for Debian/Ubuntu/RPM this is http://yourServer/lam. If you installed LAM via the tar.bz2 then this may vary. You should see the following page:
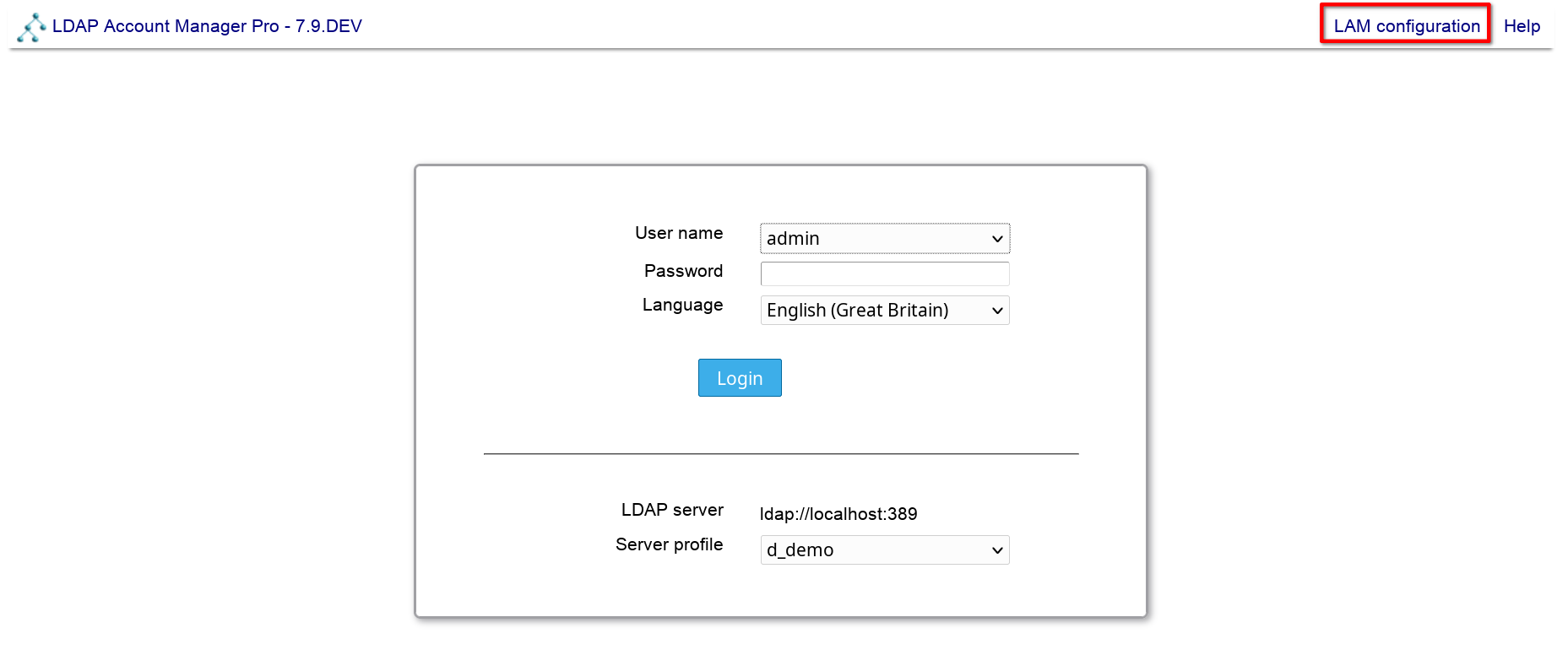
If you see an error message then you might need to install an additional PHP extension. Please follow the instructions and reload the page afterwards.
Now you are ready to configure LAM. Click on the "LAM configuration" link to proceed.
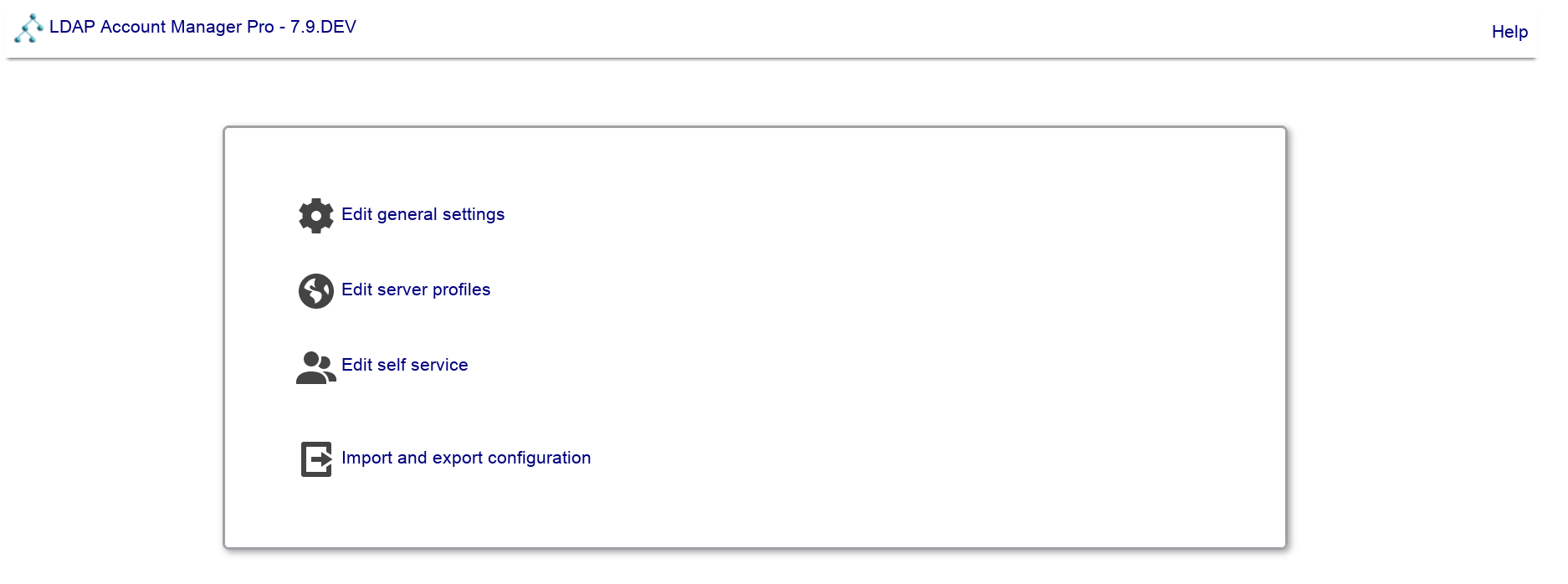
Here you can change LAM's general settings, setup server profiles for your LDAP server(s) and configure the self service (LAM Pro). You should start with the general settings and then setup a server profile.
After selecting "Edit general settings" you will need to enter the master configuration password. The default password for new installations is "lam". Now you can edit the general settings.
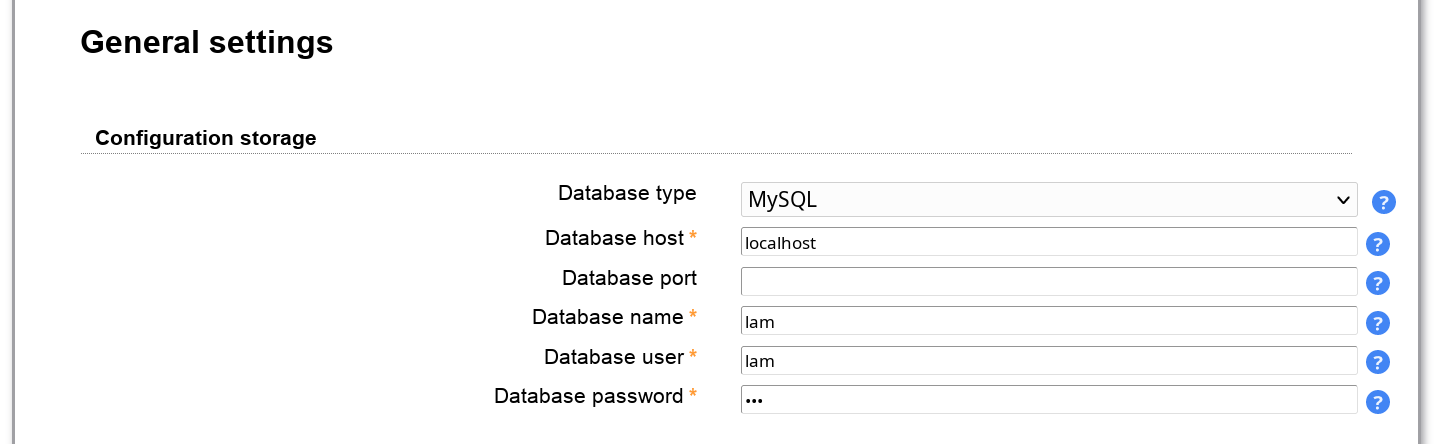
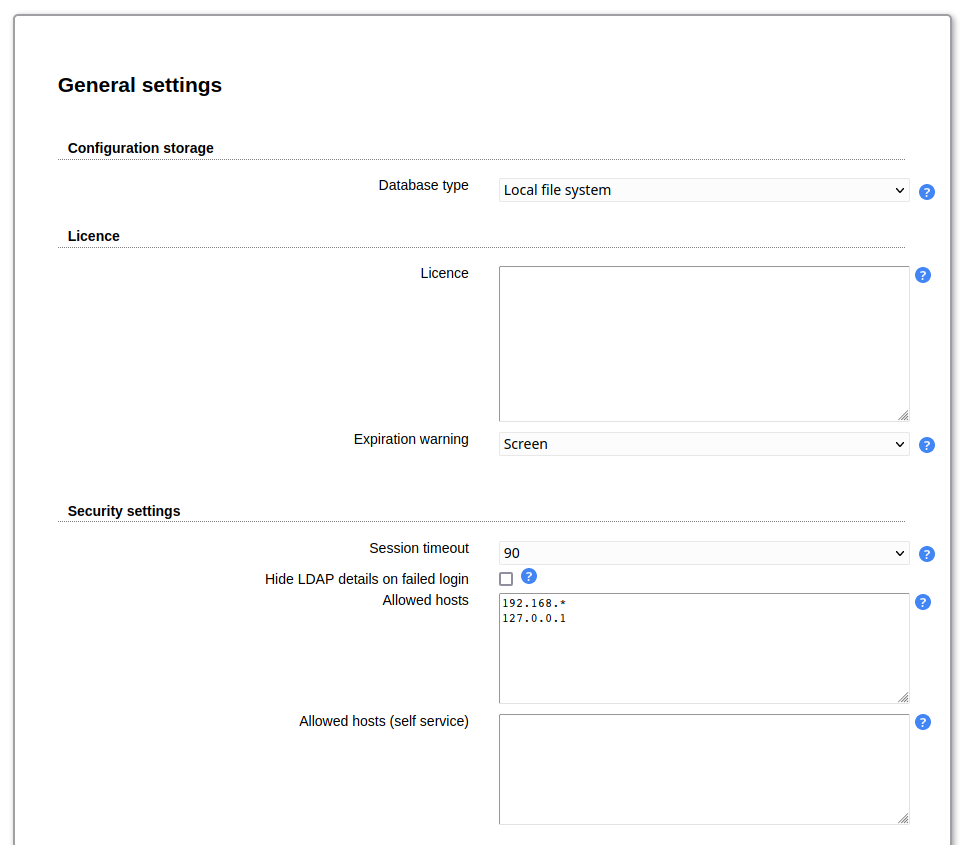
This defines where LAM should store the configuration settings. By default, local file system is used. If you have installed the PHP PDO extension incl. MySQL then you can also select MySQL here. This will then store all data (server profiles, account profiles, PDF structures, ...) in the database.
Exceptions:
Configuration storage options
LAM Pro license
CA certificates
This is very useful when running LAM cloud native e.g. inside Docker.
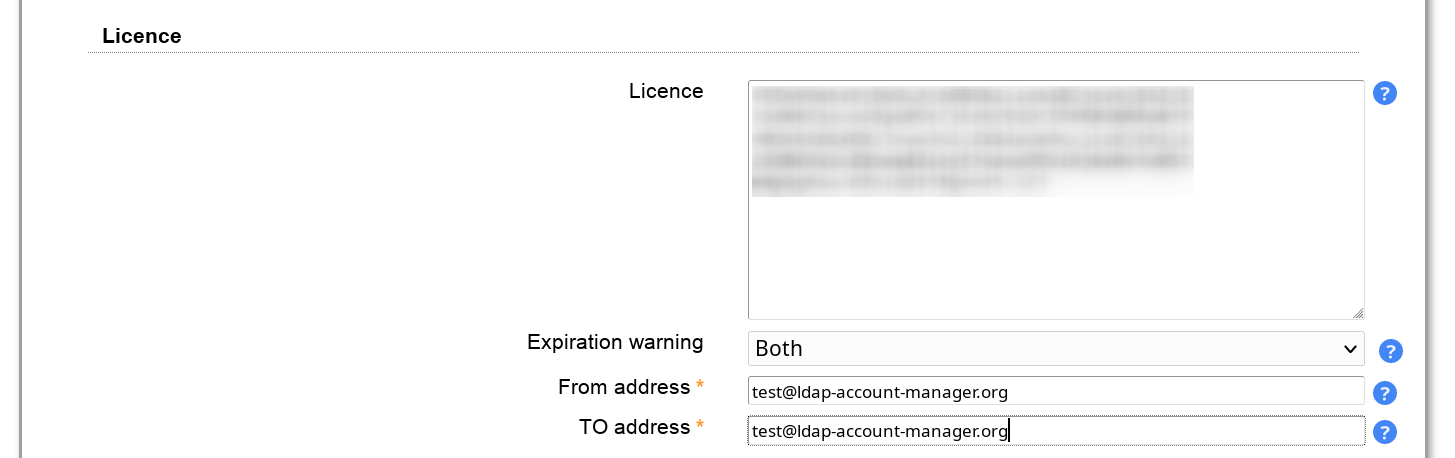
This is only required when you run LAM Pro. Please enter the license key from your customer profile. In case you have purchased multiple licenses please only enter one license key block per installation.
When you entered the license key then the license details can be seen on LAM configuration overview page.
By default, LAM Pro will show a warning message on the login page 3 weeks before expiration. You can disable this here and/or send out an email instead.
Here you can set a time period after which inactive sessions are automatically invalidated. The selected value represents minutes of inactivity.
If you do not want to expose why the login to LAM failed then activate "Hide LDAP details on failed logins". This way users will not see if their account was not found or is e.g. locked.
You may also set a list of IP addresses which are allowed to access LAM. The IPs can be specified as full IP (e.g. 123.123.123.123) or with the "*" wildcard (e.g. 123.123.123.*). Users which try to access LAM via an untrusted IP only get blank pages. There is a separate field for LAM Pro self service.
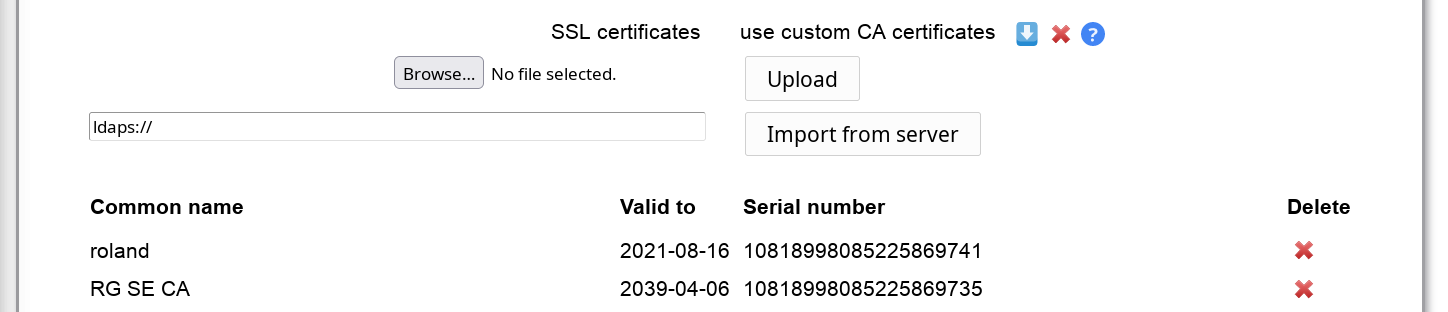
By default, LAM uses the CA certificates that are preinstalled on your system. This will work if you connect via SSL/TLS to an LDAP server that uses a certificate signed by a well-known CA. In case you use your own CA (e.g. company internal CA) you can import the CA certificates here.
Please note that this can affect other web applications on the same server if they require different certificates. There seem to be problems on Debian/Ubuntu systems and you may also need to restart Apache. In case of any problems please delete the uploaded certificates and use the system setup.
You can either upload a DER/PEM formatted certificate file or import the certificates directly from an LDAP server that is available with LDAP+SSL (ldaps://). LAM will automatically override system certificates if at least one certificate is uploaded/imported.
The whole certificate list can be downloaded in PEM format. You can also delete single certificates from the list.
Please note that you might need to restart your webserver if you do any changes to this configuration.
This allows you to specify a central password policy for LAM. The policy is valid for all password fields inside LAM admin (excluding tree view) and LAM self service. Configuration passwords do not need to follow this policy.
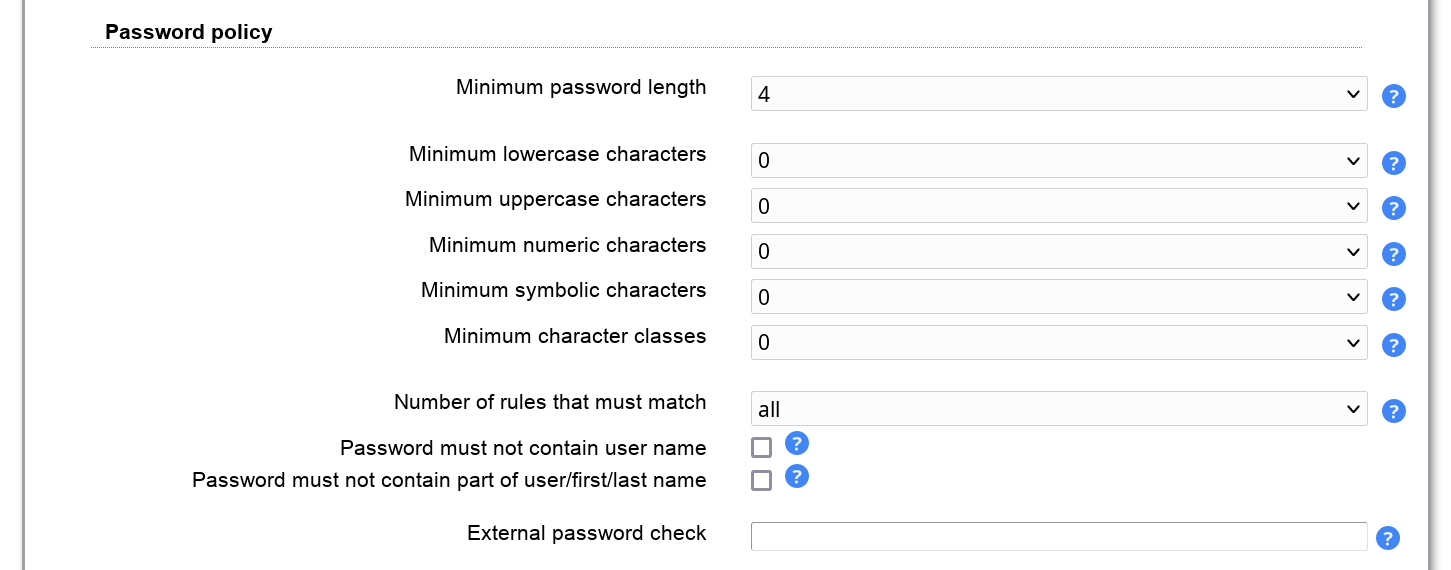
You can set the minimum password length and also the complexity of the passwords.
External password check
Please note that this option is only displayed if you have installed the PHP Curl extension for your web server.
This will validate passwords using an external service. LAM supports the protocol used by Have I been Pwned. You can use the service directly or setup any custom service with the same API. If the service reports an error LAM will log an error message and the password will be accepted.
Example URL: https://api.pwnedpasswords.com/range/{SHA1PREFIX}
LAM will build a SHA1 hash of the password and send parts of it to the service.
The configured URL must contain the wildcard "{SHA1PREFIX}" which will be replaced with the 5 character hash prefix. The service must then return a list of text lines in the format "<hash suffix>:<number>".
"<hash suffix>" needs to be the suffix of a known insecure password. The "<number>" can be any numeric value and will be ignored by LAM.
Example:
Password hash: 21BD10018A45C4D1DEF81644B54AB7F969B88D65
Hash prefix sent to service: 21BD1
Returned line: 0018A45C4D1DEF81644B54AB7F969B88D65:1
This will reject the password.
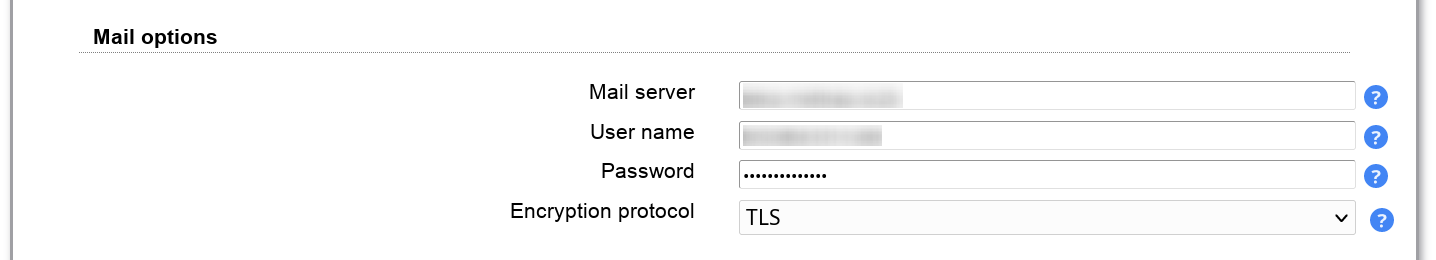
LAM can log events (e.g. user logins). You can use e.g. system logging (syslog for Unix, event viewer for Windows) or log to a separate file. Please note that LAM may log sensitive data (e.g. passwords) at log level "Debug". Production systems should be set to "Warning" or "Error".
The PHP error reporting is only for developers. By default LAM does not show PHP notice messages in the web pages. You can select to use the php.ini setting here or printing all errors and notices.
Log destinations:
File: all messages will be written to the given file. LAM will create it if not yet existing.
Syslog: uses local system logging (syslog for Unix, event viewer for Windows)
Remote: sends log messages to a remote server that supports the Unix remote Syslogd protocol. Please enter destination as "server:port", e.g. "myserver:123".
No logging: disabled logging
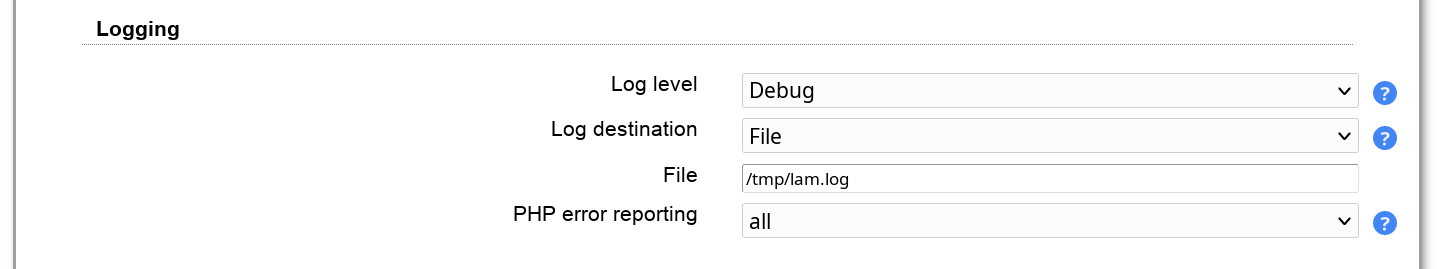
Here you can configure the mail server settings. If you do not set a mail server then LAM will try to use a locally installed one (e.g. postfix, exim, sendmail).
SMTP setup:
Mail server: enter name + port separated by ":". E.g. "server:25" will use "server" on port 25.
User name: enter the user name if your SMTP server requires authentication
Password: enter the password for the user above
Encryption protocol: Use TLS when unsure. SSL is only for older servers and deprecated. The no encryption setting should not be used for production installations.
See the WebAuthn/FIDO2 appendix for an overview about WebAuthn/FIDO2 in LAM.
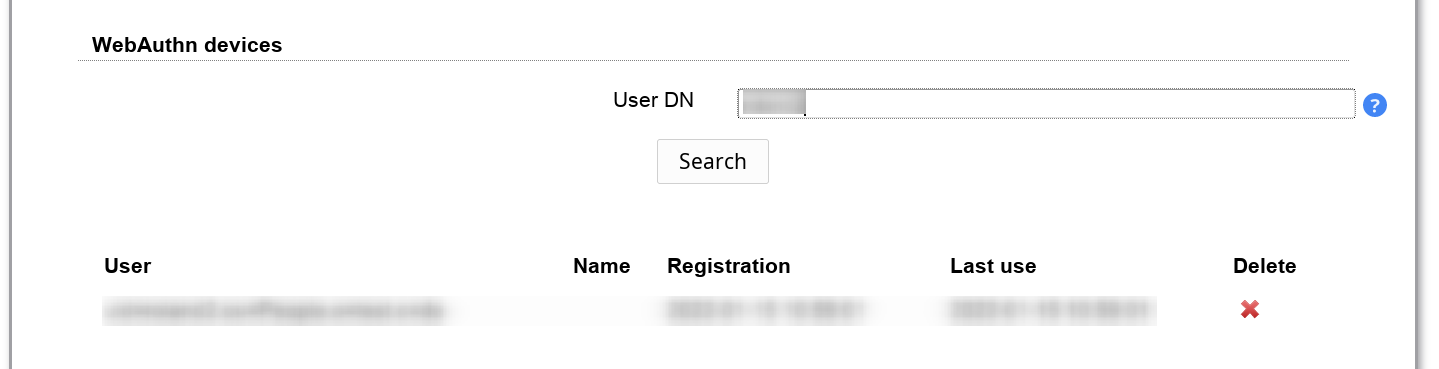
Here you can delete any webauthn device registrations. This section is only shown if at least one device is registered.
Enter a part of the user's DN in the input box and perform a search. LAM will show users and devices that match the search. You can then delete a device registration. If the user has no more registered devices then LAM will ask for registration on next login.
Note: You cannot add any device here. This can only be done by the user during login, webauthn tool or self service.